For my Master’s thesis, I spent almost half a year investigating Apple Intelligence and Private Cloud Compute. I started my thesis in October 2024, when Apple Intelligence was still very young and not even available on iPhones in the EU. The security/privacy issue I discovered and describe here is – to the best of my knowledge – the first issue in the context of Apple Intelligence ever acknowledged and fixed by Apple.
Security & Transparency
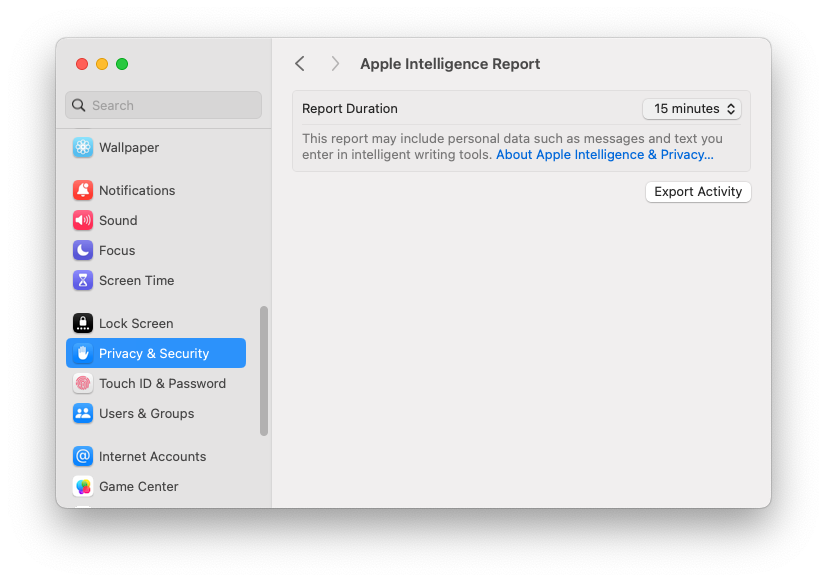
Apple gladly portrays itself as a privacy-focused company and as such, processing Apple Intelligence requests in the cloud in plaintext is a tricky undertaking. Its cloud infrastructure – Private Cloud Compute (PCC) – therefore also comes with specific promises towards user privacy and security. One of these is transparency: users must be able to see which requests are processed on PCC and what data is sent there. While it is sadly not possible to check this beforehand or disable cloud processing entirely, there is at least a way to find it out afterward. That’s where Apple Intelligence Reports come in.
Apple Intelligence Reports (AIRs)
AIRs are enabled by default and set to capture the last 15 minutes. It is also possible to set the time window to 7 days or turn the logging off entirely in System Settings > Privacy & Security > Apple Intelligence Report.
To obtain the report, we must click the Export Activity button in the settings and are prompted to choose a location where the JSON file should be saved.
Here is an example of an AIR that I exported after summarizing an email:
| |
So, there are essentially two things included in such an AIR: the request prompt with the generated response, and details on the PCC node that handled the request. As you can see in line 8, the prompt also contains potentially sensitive data, in this case the subject and body of the email.
The Issue
During my investigation, I wanted to find out where all this request data is being stored, so that it can be collected and exported as an AIR later.
For that, I had the fs_usage tool running while I navigated through the steps of exporting the report. 1
Going through the recorded logs, I noticed a file called Apple_Intelligence_Report.json being written to the path /private/var/folders/vg/<random>/T, even though I didn’t actually choose a location in the settings, but instead selected Cancel.
This directory, as I later found out, is just the user’s home directory and defined in the $TMPDIR environment variable or easily accessible in Swift through:
FileManager.default.temporaryDirectory
As such, this path is readable and writable by any application which runs with user-level permissions (i.e., almost all apps) and which isn’t sandboxed (i.e., most apps on macOS). 2
Potential Impact
The impact is obvious: a malicious app installed on the user’s Mac could routinely check the user’s temporary directory for the AIR file and extract potentially sensitive information from it. The file is present there until the device is restarted – a simple logout and re-login doesn’t clear the directory. However, user interaction is still required in some form, as the user first needs to click the Export Activity button, which I suppose only few people actually do.
Responsible Disclosure Timeline
- February 12, 2025: Discovered the issue
- February 13, 2025: Discussed it with my supervisor and reported the issue to Apple
- a few days later: Apple reproduced the issue
- April 8, 2025: Apple plans to release a fix in spring 2025
- May 12, 2025: macOS 15.5 is released, fixing the issue
Unfortunately, I did not receive a bounty from Apple.
It turned out the Biome subsystem is responsible for this. hoakley wrote a very good overview of Biome a while back. ↩︎
This second requirement is also the reason why iOS and iPadOS aren’t affected by this issue, because all apps installed there must be sandboxed and thus have their own temporary directory. ↩︎